4. Getting Started - Plan
4. Start with Planning
The SAF's main pillars are Plan, Harden, Validate, Normalize, and Visualize. First, it is necessary to plan what components will be in your system and identify the security guidance available for those components.

4.1 Identify your stack of components for the system
Your software system is composed of multiple components. i.e., Cloud Services, Virtualization Platforms, Operating Systems, Databases, Application Logic, and Web Servers.
The first step of any assessment is identifying the components for the system you are assessing.
4.2 What is the guidance?
There could be Security Technical Implementation Guides (STIGs), Security Requirements Guides (SRGs), Center for Internet Security (CIS) Benchmarks, or vendor guidance written for the components in your software stack. Being aware of these can help inform which profile to use. Additionally, note here any specific requirements for your organization that might differ from the specific published guidance. This will inform how to tailor the profiles later on.
4.3. Content libraries for software components
As you saw in the previous section's SAF Site scavenger hunt, the SAF website hosts links, informaiton, and tools to ease the security process. To get a better idea of what may be in your software stack and what kind of content is available for automated testing, you can peruse the SAF's hardening and validation content libraries when you are making a plan.
Go to saf.mitre.org
Go to the SAF site to peruse the hardening and validation libraries. As the security community develops more automation content, we update this site as a landing page for all of the content. The site will look like this:
Peruse Hardening Content
Navigate to the Harden page to find library content for hardening different software components. Hardening content is software used to configure a component to comply with security guidance.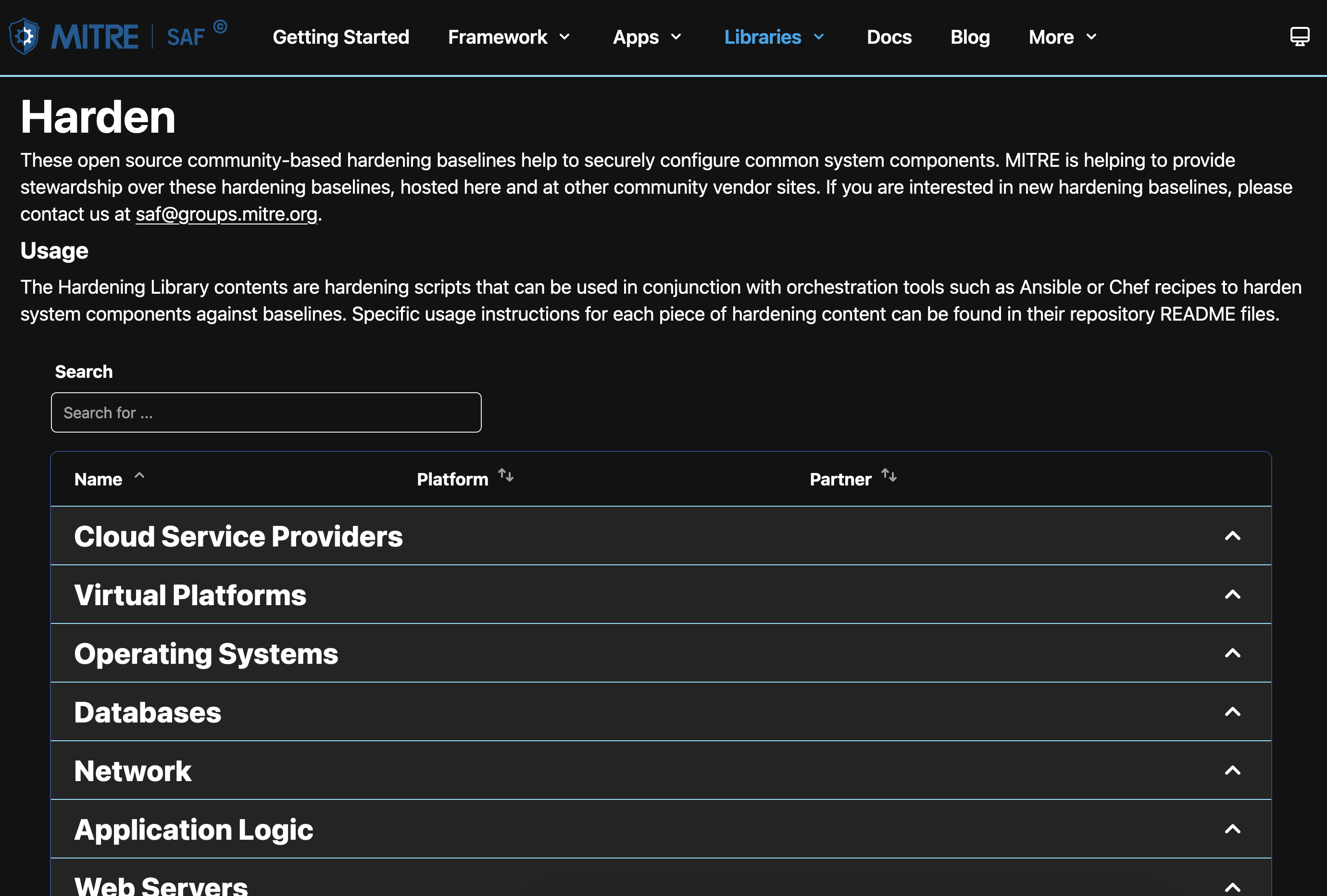
Peruse Validation Content
Navigate to the Validate page to find library content for validating different software components against security guidance. Validation content is software used to test whether the component is configured to some security guidance. We will be looking more at the Validation library in a moment.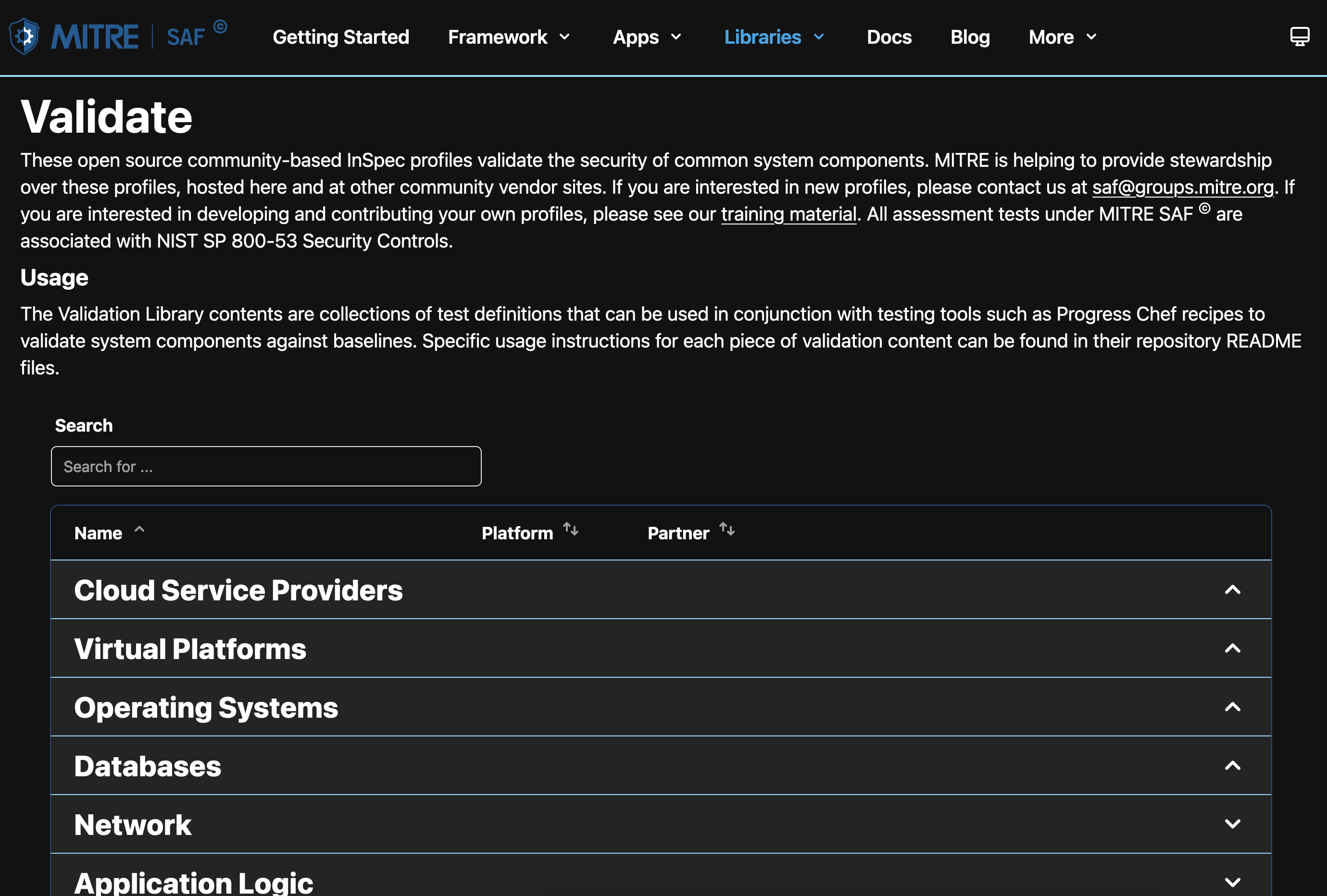
4.4. What if there is no content for a software component?
- First, reach out to the SAF team at saf@groups.mitre.org to find out if there is a profile in development or otherwise available but not listed that could meet your needs.
- Second, if there is still no profile available, identify the security guidance to which the profile should comply and reach out to find out how to best create that profile. We help teams do this and provide training courses on that as well!
- Third, if there is no guidance available for your particular component, talk with us about developing the guidance using MITRE's Vulcan application. Reference the training class on security guidance development.