11. Comparing Results
11. Comparing Results
11.1 Validate the software after hardening
Now that we have hardened the software, we need to run InSpec again to see the results.
Let's change directories to get back to the root directory.
cd /workspaces/saf-training-lab-environment/
Now, rerun the InSpec scan with a different file name by changing the --reporter to have a new file name indicating that these are the hardened results like this: --reporter cli json:./results/nginx_hardened_results.json.
inspec exec https://github.com/mitre/nginx-stigready-baseline -t docker://nginx --reporter cli json:./results/nginx_hardened_results.json --input-file inputs.yml
11.2 CLI Results
After running the command, you should see different results than when we ran the vanilla InSpec scan.
inspec exec https://github.com/mitre/nginx-stigready-baseline -t docker://nginx --reporter cli json:./results/nginx_hardened_results.json --input-file inputs.yml
[2022-09-26T12:33:00+00:00] WARN: URL target https://github.com/mitre/nginx-stigready-baseline transformed to https://github.com/mitre/nginx-stigready-baseline/archive/master.tar.gz. Consider using the git fetcher
...
↺ V-56019: An NGINX web server utilizing mobile code must meet DoD-defined mobile code
requirements.
↺ This check is NA because NGINX does not implement mobile code.
↺ V-56021: The NGINX web server must invalidate session identifiers upon hosted
application user logout or other session termination.
↺ This test requires a Manual Review: Verify it invalidates session identifiers when a
session is terminated by reviewing the NGINX documentation.
↺ V-56025: Cookies exchanged between the NGINX web server and client, such as session
cookies, must have security settings that disallow cookie access outside the
originating web server and hosted application.
↺ This check is NA because the proxy_cookie_path directive is not configured.
✔ V-56027: The web server must only accept client certificates issued by DoD PKI
or DoD-approved PKI Certification Authorities (CAs).
✔ [["/etc/ssl/nginx-selfsigned.pem"]] is expected not to be nil
✔ x509_certificate /etc/ssl/nginx-selfsigned.pem is expected not to be nil
✔ x509_certificate /etc/ssl/nginx-selfsigned.pem subject.C is expected to cmp == "US"
✔ x509_certificate /etc/ssl/nginx-selfsigned.pem subject.O is expected to cmp == "U.S. Government"
✔ DoD is expected to be in "DoD" and "ECA"
↺ V-56029: The NGINX web server must augment re-creation to a stable and known
baseline.
↺ This test requires a Manual Review: Interview the SA and ask for documentation on the
disaster recovery methods for the NGINX web server in the event of the necessity for rollback.
↺ V-56031: The NGINX web server must encrypt user identifiers and passwords.
↺ This check is NA because NGINX does not manage authentication.
✔ V-56033: The web server must install security-relevant software updates within
the configured time period directed by an authoritative source (e.g., IAVM,
CTOs, DTMs, and STIGs).
✔ NGINX version v1.23.1 installed is not more then one patch level behind v1.23.0 is expected to cmp >= "1.23.0"
✔ NGINX version v1.23.1 installed is greater then or equal to the organization approved version v1.23.1 is expected to cmp >= "1.23.1"
✔ V-56035: The NGINX web server must display a default hosted application web page, not
a directory listing, when a requested web page cannot be found.
✔ The root directory /usr/share/nginx/html should include the default index.html file.
✔ V-61353: The web server must remove all export ciphers to protect the
confidentiality and integrity of transmitted information.
✔ The ssl_prefer_server_cipher should be set to on.
✔ Each cipher found in configuration should be included in the list of ciphers approved to encrypt data
✔ Each cipher found in configuration should be included in the list of ciphers approved to encrypt data
✔ Each cipher found in configuration should be included in the list of ciphers approved to encrypt data
✔ Each cipher found in configuration should be included in the list of ciphers approved to encrypt data
✔ Each cipher found in configuration should be included in the list of ciphers approved to encrypt data
✔ Each cipher found in configuration should be included in the list of ciphers approved to encrypt data
✔ Each cipher found in configuration should be included in the list of ciphers approved to encrypt data
✔ Each cipher found in configuration should be included in the list of ciphers approved to encrypt data
✔ Each cipher found in configuration should be included in the list of ciphers approved to encrypt data
✔ Each cipher found in configuration should be included in the list of ciphers approved to encrypt data
✔ Each cipher found in configuration should be included in the list of ciphers approved to encrypt data
✔ Each cipher found in configuration should be included in the list of ciphers approved to encrypt data
✔ Each cipher found in configuration should be included in the list of ciphers approved to encrypt data
✔ Each cipher found in configuration should be included in the list of ciphers approved to encrypt data
✔ Each cipher found in configuration should be included in the list of ciphers approved to encrypt data
✔ Each cipher found in configuration should be included in the list of ciphers approved to encrypt data
✔ Each cipher found in configuration should be included in the list of ciphers approved to encrypt data
✔ Each cipher found in configuration should be included in the list of ciphers approved to encrypt data
✔ Each cipher found in configuration should be included in the list of ciphers approved to encrypt data
✔ Each cipher found in configuration should be included in the list of ciphers approved to encrypt data
Profile Summary: 62 successful controls, 3 control failures, 24 controls skipped
Test Summary: 303 successful, 3 failures, 24 skipped
11.3 Download the Results File
As you did before, download the results file.
11.3.1 Multiple Files in Heimdall?
If you reopened Heimdall to upload your nginx_hardened_results.json, then there will only be one file loaded. However, if you uploaded the results to the same instance of Heimdall that you had open before, you will now see two sets of results - your vanilla results and hardened results. You can click the menu on the top left what files are loaded and select only those you wish to see. In this case, only select the hardened results so we can look more at those.
Heimdall with a backend (server)
Throughout this class, we are using the Heimdall-lite version of the Heimdall application. However, many organizations chose to deploy Heimdall with a backend (you can see a demo version here), in other words, with a server to store data. This requires more setup than just opening up Heimdall-lite in the webpage, however, you can:
- Store files in a database
- Send files to the app via an API call
- Share information across multiple users
- Login via third part authenticators, like Keycloak.
You can find out more details on the difference between the two versions of this application in the Heimdall README.
Take some time to explore the hardened results. Filter through different statuses, checkout the alignment to NIST 800-53 controls, and more!
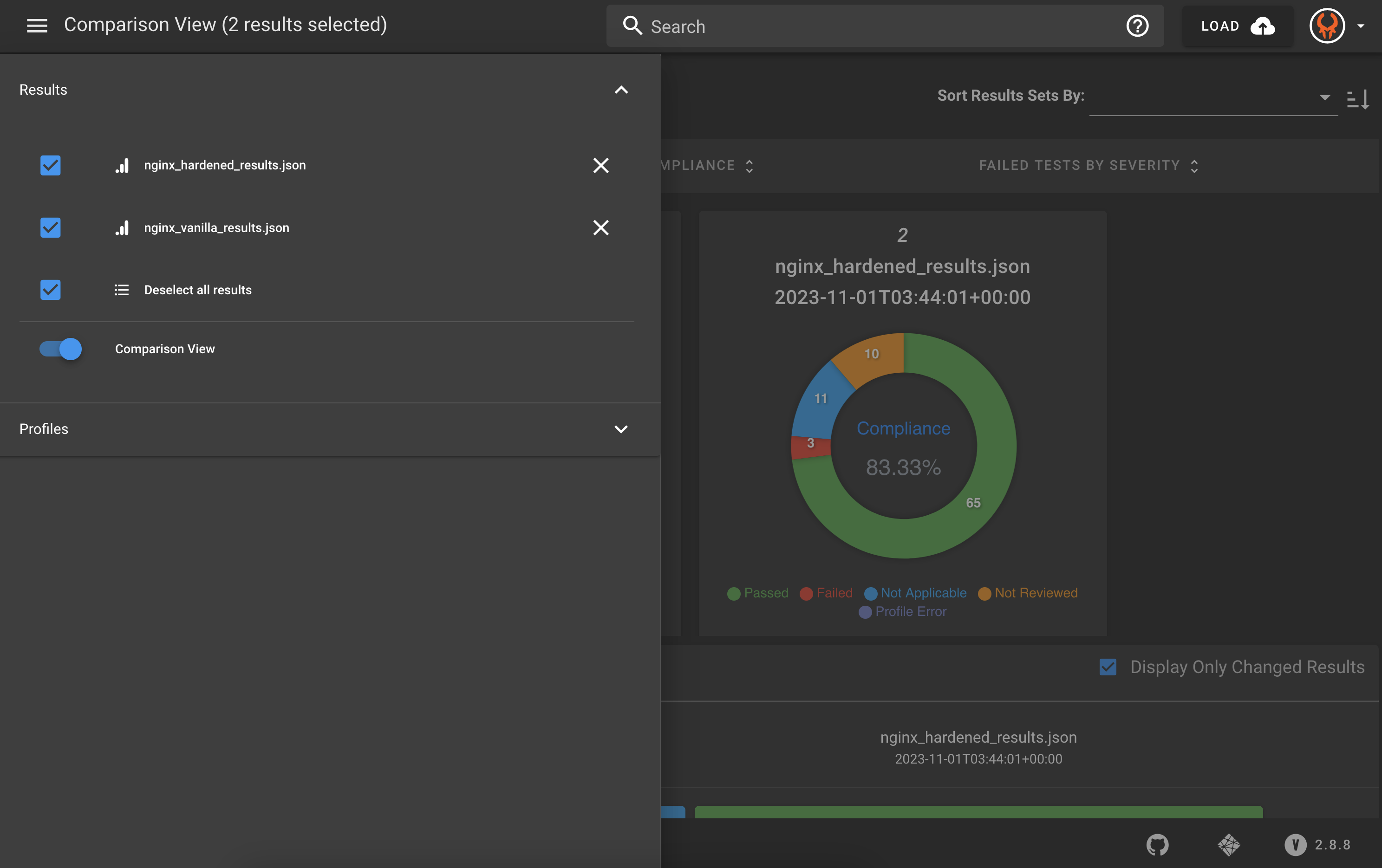
11.4 Visualize the Results in Heimdall
Another valuable view for monitoring changes and showing results is the comparison view.
- Make sure you have both the vanilla and hardened results uploaded into Heimdall.
- To compare results, click on the three lines in the top, left corner and toggle the "Comparison View" on.
- Explore what changed and why!
You could use the Heimdall with backend version of the application and upload security results at regular intervals to see the changes over time. There are two graphs that show compliance over time and number of failed tests by severity over time.