Today’s decision makers and computer and network defense (CND) professionals face an environment with several key challenges:
Adversarial Tactics, Techniques, and Common Knowledge (ATT&CK) is a model and framework for describing the actions an adversary may take while operating within an enterprise network. The model can be used to better characterize and describe post-compromise adversary behavior. It both expands the knowledge of network defenders and assists in prioritizing network defense by detailing the post-compromise (post-exploit and successful access) tactics, techniques, and procedures that advanced persistent threats use to execute their objectives while operating inside a network.
Our methodology for better detecting adversary activity is an iterative process:
The Cyber Analytics Repository (CAR) is a knowledge base of analytics developed by The MITRE Corporation. The analytics detect ATT&CK techniques using data from various sensors.
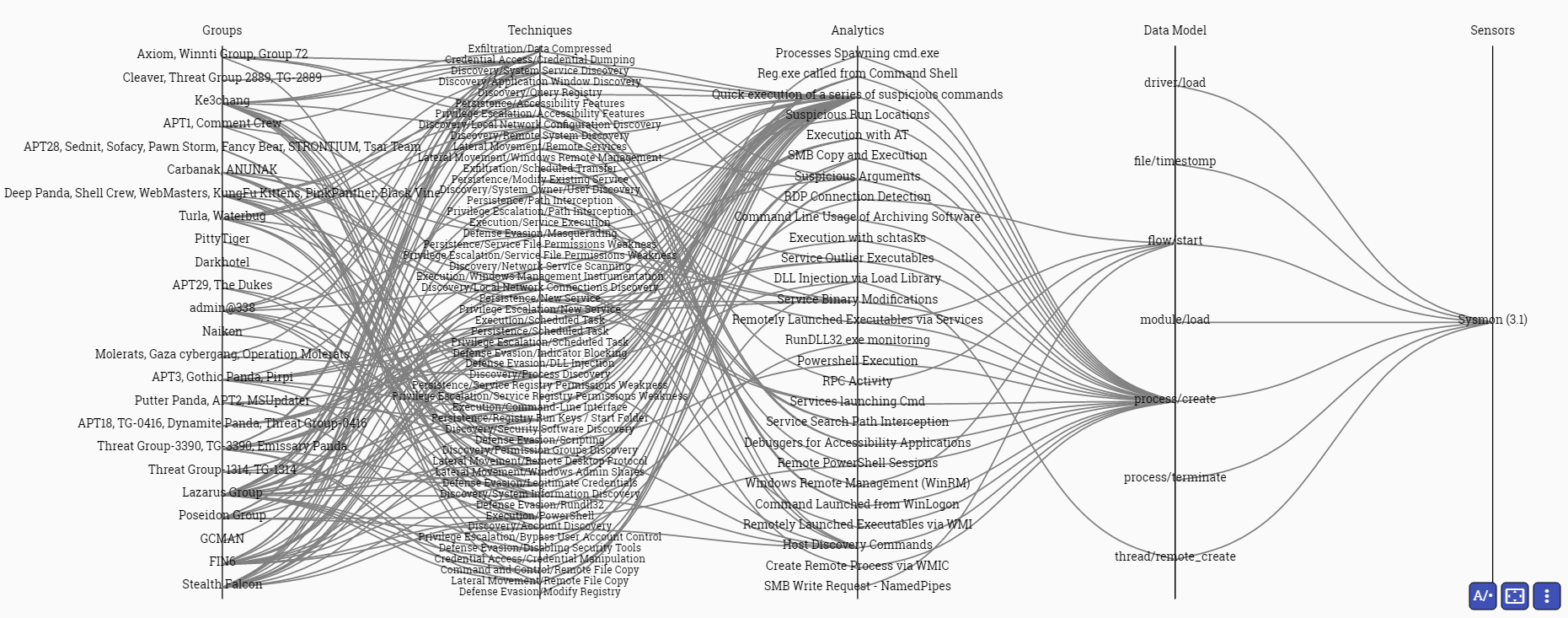
The Cyber Analytic Repository Exploration Tool (CARET) is a proof-of-concept graphical user interface designed to connect the groups and techniques highlighted in ATT&CK to the analytics, data model, and sensors highlighted in CAR. CARET is used to develop an understanding of defensive capabilities and to aid in their development and use.
The following image depicts deploying the Microsoft® Sysmon 3.0 sensor in an enterprise. By deploying this sensor, the analytics shown enable an analyst to identify a variety of ATT&CK techniques and the groups that use those techniques.
Unfetter is an open-source software project that expands upon CARET to help cyber security professionals identify and analyze defensive gaps in a more repeatable way. For more information about Unfetter, please see the NSA Unfetter GitHub page.
Check out our Releases page to try out the tools.
Additional information about CAR and ATT&CK to help you understand the concepts behind Project Unfetter may be found at https://car.mitre.org and https://attack.mitre.org
1 A blue team consists network defenders who use analytics to detect red team (adversary) activity. They may be thought of as a hunting team.